The T2 Scam has become a significant concern for many individuals and businesses alike. With the rise of digital transactions and online services, scammers are finding new and innovative ways to exploit unsuspecting victims. Understanding the mechanisms of the T2 Scam is crucial for anyone who uses online platforms, as it can have severe financial repercussions and emotional distress. In this article, we will delve into the complexities of the T2 Scam, explore its various forms, and provide essential tips to safeguard yourself against potential threats.
As technology continues to evolve, so do the tactics used by scammers. The T2 Scam is a prime example of how fraudsters leverage technology to deceive individuals and organizations. This article aims to shed light on the intricacies of this scam, offering insights into its operational methods and providing readers with the tools necessary for protection. By the end of this article, you will have a comprehensive understanding of the T2 Scam, its implications, and how to stay safe.
In our in-depth exploration, we will address common questions and concerns regarding the T2 Scam. We will also present data and statistics that highlight the prevalence of this issue, ensuring that you are well-informed. Knowledge is power, and by arming yourself with information, you can take proactive measures to avoid falling victim to the T2 Scam.
Table of Contents
What is the T2 Scam?
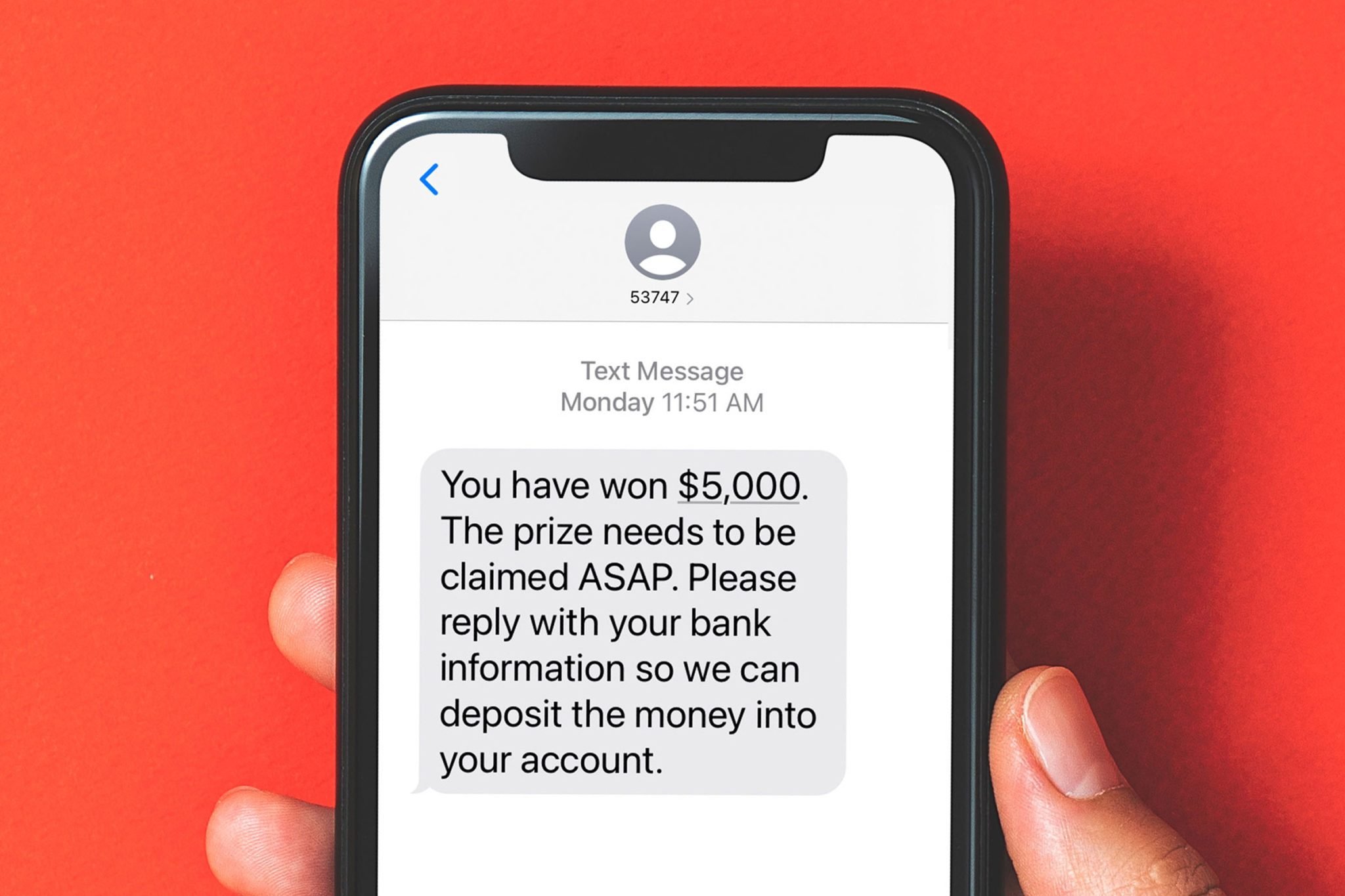
The T2 Scam refers to a specific type of fraud that typically involves impersonation and deceit to gain access to sensitive information or financial resources. It often manifests through emails, phone calls, or text messages that appear to be from legitimate organizations, such as banks or government entities. Victims are usually tricked into providing personal or financial information, which is then used for fraudulent purposes.
Key Characteristics of T2 Scams
- Impersonation of reputable organizations
- Urgent calls to action
- Requests for sensitive information
- Use of emotional manipulation
Types of T2 Scams
T2 Scams can take various forms, each with distinct methods and targets. Below are some common types of T2 Scams:
1. Phishing Scams
Phishing scams involve fraudulent emails or messages that appear to come from legitimate sources, tricking individuals into providing personal information.
2. Impersonation Scams
Scammers may impersonate a trusted individual or organization, convincing victims to send money or share sensitive data.
3. Investment Scams
These scams often promise high returns on investments and require individuals to invest money upfront. They are usually too good to be true.
How the T2 Scam Works
The T2 Scam operates through a series of deceptive tactics designed to manipulate victims. Here’s a breakdown of how it typically works:
Step 1: Initial Contact
Scammers initiate contact through various channels, such as email or phone calls, often using spoofed numbers or email addresses to appear legitimate.
Step 2: Building Trust
Once contact is made, scammers work to establish trust by providing credible information or creating a sense of urgency that prompts quick action from the victim.
Step 3: Request for Information
Victims are then asked to provide sensitive information, such as login credentials or financial details, under the guise of verifying their identity or processing a transaction.
Signs of a T2 Scam
Recognizing the signs of a T2 Scam can help you avoid becoming a victim. Here are some red flags to watch out for:
- Unsolicited communication from unknown sources
- Requests for personal or financial information
- Urgent language demanding immediate action
- Offers that seem too good to be true
Impact of the T2 Scam
The consequences of falling victim to a T2 Scam can be devastating. Victims may experience significant financial loss, identity theft, and emotional distress. According to recent studies, scams like the T2 Scam have resulted in billions of dollars in losses annually.
How to Protect Yourself from the T2 Scam
Protection against T2 Scams involves a combination of vigilance and proactive measures. Here are some strategies to help safeguard yourself:
- Verify the source of communication before providing any information.
- Use two-factor authentication for online accounts.
- Educate yourself about common scams and their tactics.
- Report suspected scams to relevant authorities.
Reporting the T2 Scam
If you suspect that you have been targeted by a T2 Scam, it is essential to report it to the appropriate authorities. This can help prevent others from becoming victims and assist in tracking down the perpetrators.
Conclusion
In conclusion, the T2 Scam represents a significant threat in today's digital landscape. By understanding its mechanisms, recognizing the signs, and taking proactive measures, you can protect yourself from becoming a victim. If you have any experiences or tips related to the T2 Scam, please share them in the comments below. Together, we can create a community of awareness and support.
Final Thoughts
Thank you for reading our comprehensive guide on the T2 Scam. We hope this article equips you with the knowledge needed to stay safe. Be sure to check back for more informative articles and share this with your network to spread awareness!
Article Recommendations


ncG1vNJzZmilqZu8rbXAZ5qopV%2BcrrOwxKduaKxdZ3q0r8CmZaGsnaE%3D